Table of Contents
ToggleCourier – TOR Scam Report (2)
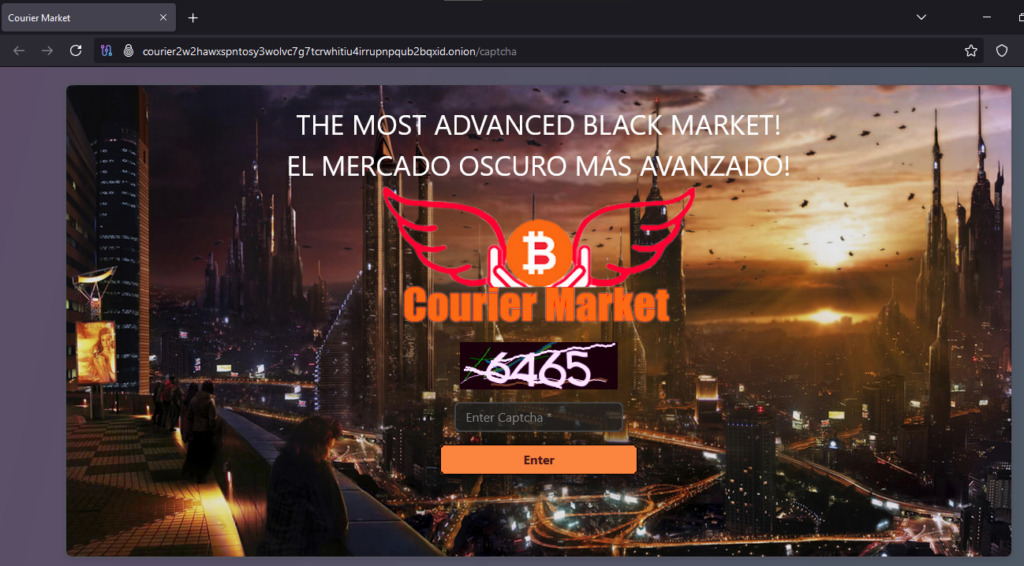
Onion Link : http://courier2w2hawxspntosy3wolvc7g7tcrwhitiu4irrupnpqub2bqxid.onion/captcha
Scam Report Date : 2024-11-08
Client Scam Report Breakdown
Original Scam Report :
The client reported that their Bitcoin holdings were stolen on two separate occasions due to a PMI (Private Message Interception) attack and an insider orchestrating a breach of PGP (Pretty Good Privacy) two-factor authentication. These incidents highlight severe security vulnerabilities and deliberate exploitation of trust within a system or platform. The PMI attack likely involved intercepting or manipulating private communications to deceive the victim, while the insider’s role suggests collusion and deliberate bypassing of cryptographic protections. These types of scams are increasingly sophisticated and exploit both technical and human factors to gain unauthorized access to cryptocurrency assets.
Definitions and Terminology
- Bitcoin (BTC): A decentralized digital currency that relies on blockchain technology to facilitate secure peer-to-peer transactions. It is often targeted by cybercriminals due to its pseudonymous nature and high value.
- PMI Attack (Private Message Interception): A form of attack where a third party intercepts or manipulates private communications between two parties. In the context of cryptocurrency, this can involve spoofing messages or rerouting transaction details to steal funds.
- PGP (Pretty Good Privacy): A robust encryption tool used for secure communication and data protection. PGP can also be integrated with two-factor authentication to enhance security. Breaching such systems typically involves exploiting human error, technical vulnerabilities, or insider access.
- Two-Factor Authentication (2FA): An additional layer of security requiring users to verify their identity using two separate methods, such as a password and a cryptographic key or biometric data. Circumventing this often necessitates a high level of access or sophisticated hacking techniques.
- Insider Attack: A malicious act perpetrated by someone within the organization or system with authorized access to critical information or resources. Such attacks are particularly challenging to detect and prevent.
This report underscores how cybercriminals blend technical expertise with social engineering or collusion to breach even robust security measures. By intercepting private messages and bypassing PGP-based two-factor authentication, the attackers demonstrated both knowledge of the victim’s system and an ability to manipulate or exploit it effectively.
Analysis and Recommendations
The dual attacks in this case highlight the importance of implementing advanced security measures and maintaining vigilance to safeguard cryptocurrency holdings. To mitigate the risk of similar breaches, users and organizations should consider the following recommendations:
- Strengthen Communication Channels: Employ end-to-end encrypted messaging systems that are resistant to interception or manipulation. Avoid sharing sensitive transaction details over unsecured or unverified platforms.
- Enhance Two-Factor Authentication: Use multi-layered security measures, such as hardware-based tokens (e.g., YubiKeys) or biometric authentication, which are harder to compromise than software-based 2FA systems.
- Conduct Regular Security Audits: Organizations handling cryptocurrency should perform frequent assessments of internal systems and protocols to detect and mitigate vulnerabilities.
- Mitigate Insider Threats: Establish stringent access controls and monitoring systems to detect unusual activity from authorized personnel. Employees should undergo background checks, and sensitive operations should involve multi-party verification.
- Educate Users: Provide training on recognizing phishing attempts, the importance of secure communication, and best practices for safeguarding private keys and recovery phrases.
This incident also serves as a cautionary tale about the dangers of over-relying on single-layer security measures or assuming that encryption alone is sufficient to deter attackers. As cryptocurrency becomes a more integral part of digital finance, the sophistication of attacks will continue to grow. A combination of cutting-edge technology, vigilant user practices, and organizational oversight is essential for staying ahead of evolving threats.
By understanding and addressing the mechanisms behind these attacks, stakeholders can develop more resilient systems and reduce the likelihood of such breaches in the future. Enhanced security awareness and proactive measures remain key in protecting assets and maintaining trust in cryptocurrency ecosystems.