Table of Contents
ToggleAlpha Cards – TOR Scam Report (86)
Onion Link : http://alpha6fwbu5fh5w4btl7c4fbfvfortehsi63d3bbacb4cedqittmnnqd.onion/
Scam Report Date : 2025-01-12
Client Scam Report Breakdown
Original Scam Report :
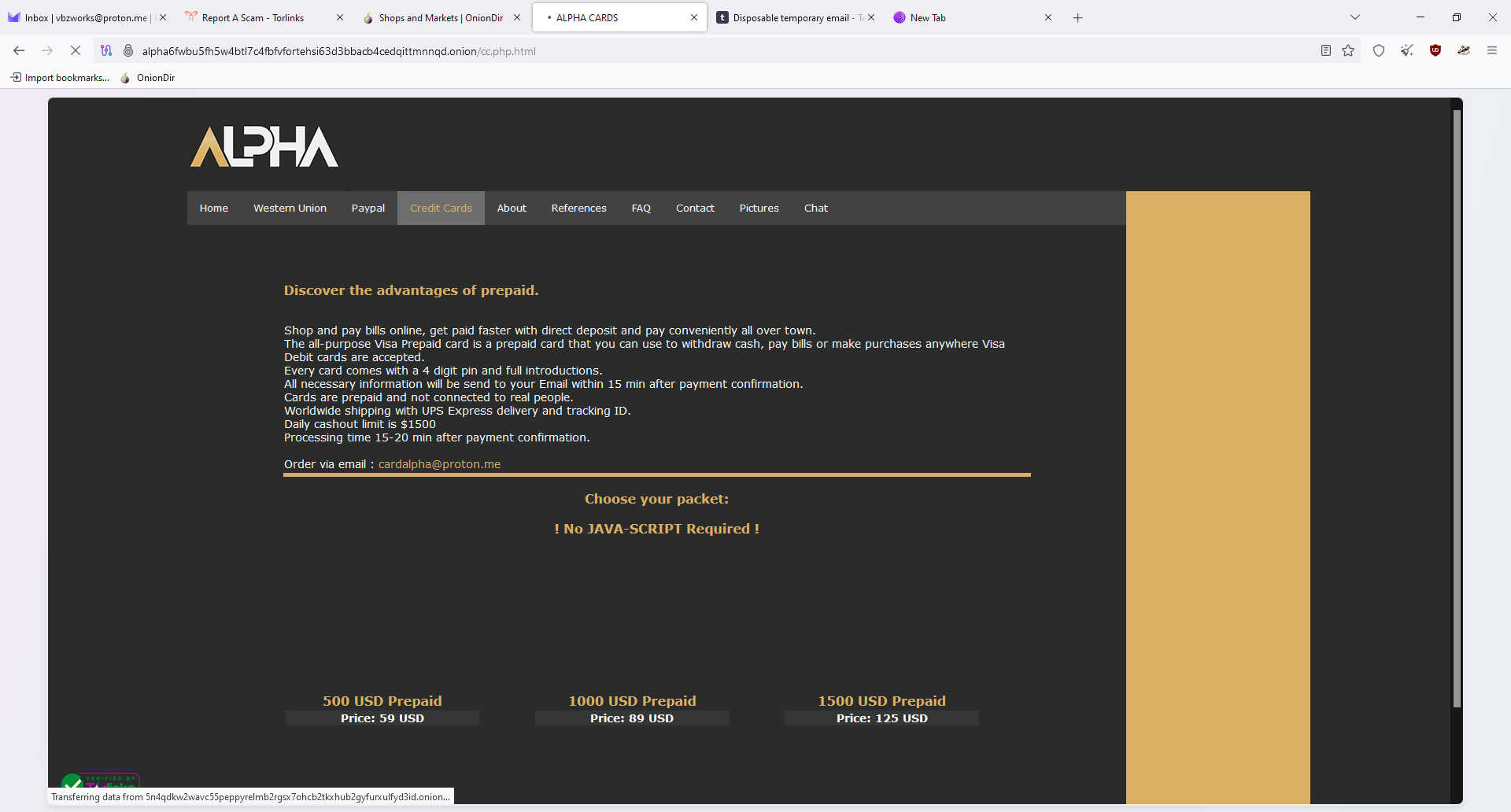
The original scam report provides critical insights into the fraudulent practices of a reported individual or entity. The report accuses the subject of engaging in fraudulent activities by selling purportedly stolen credit cards and using phishing techniques to deceive victims. Additionally, the report provides evidence of a recurring pattern of fraud, with a specific reference to a link showcasing the repeated use of the same email address for phishing schemes.
The report highlights a dual approach to scamming: (1) selling fake or stolen financial instruments, specifically credit cards, and (2) employing phishing tactics to extract sensitive information from unsuspecting individuals. The mention of a consistent email address linked to these schemes points to a lack of sophisticated operational tactics, possibly indicating either carelessness or overconfidence in evading detection.
Photos :
II. Analysis and Definition of Key Terminology
To better understand the scam’s scope and methodology, it is essential to define the key terms used in the report:
- Scammar: A colloquial term derived from “scam,” indicating the act of defrauding or deceiving someone, typically for financial gain. In this context, the scammer engages in selling stolen or fake credit cards under false pretenses.
- Supuestas Tarjetas de Crédito Robadas: Translates to “supposedly stolen credit cards.” This term implies that the scammer markets these cards as stolen to attract buyers looking to use fraudulent financial instruments. Whether the cards are genuinely stolen or entirely fabricated remains uncertain, as both would serve the scammer’s purposes.
- Correo Electrónico: Refers to an email address. The report highlights that the same email address is used across multiple fraudulent activities, including phishing schemes, signaling a link between various scams conducted by the individual or group.
- Phis: Likely shorthand for “phishing,” a deceptive tactic where scammers impersonate legitimate entities to trick individuals into sharing sensitive information such as passwords, credit card details, or personal identification numbers. Phishing is often executed via emails, fake websites, or text messages designed to mimic trusted sources.
- Enlace: A link provided in the report, purportedly serving as evidence of the scammer’s activities. This link may contain records of their phishing attempts, promotional materials for stolen credit cards, or other incriminating information linking the scammer to the reported fraud.
III. Implications and Concluding Remarks
The practices outlined in this scam report reveal a calculated approach to financial fraud, combining stolen financial instruments with phishing tactics to maximize potential gain. By selling “supposedly stolen credit cards,” the scammer not only preys on individuals seeking to exploit illicit goods but also runs the risk of defrauding these buyers if the cards are fake or unusable. This dual-layered deception further emphasizes the scammer’s intent to exploit every opportunity for profit, regardless of the victim’s intent.
The consistent use of the same email address across scams highlights a critical vulnerability in the scammer’s operation. Such repetition enables investigators, cybersecurity professionals, and victims to trace patterns and consolidate evidence. Furthermore, phishing, as identified in the report, is a significant cybercrime often leading to identity theft, financial loss, and reputational damage for victims. The scammer’s reliance on phishing indicates their strategy to directly exploit victims’ trust while augmenting their fraudulent financial schemes.
In conclusion, this report provides compelling evidence of a multi-faceted scam operation targeting vulnerable individuals. By analyzing the terminology and behaviors described, it becomes clear that this entity employs rudimentary yet effective techniques to deceive and defraud. The report underscores the importance of vigilance when interacting with unknown entities online and highlights the critical role of community reporting in exposing and combating cybercrime. Efforts to investigate the provided evidence, such as the shared link and email address, could be pivotal in dismantling this operation and preventing further victimization.