Table of Contents
ToggleDark Web Hackers – TOR Scam Report (96)
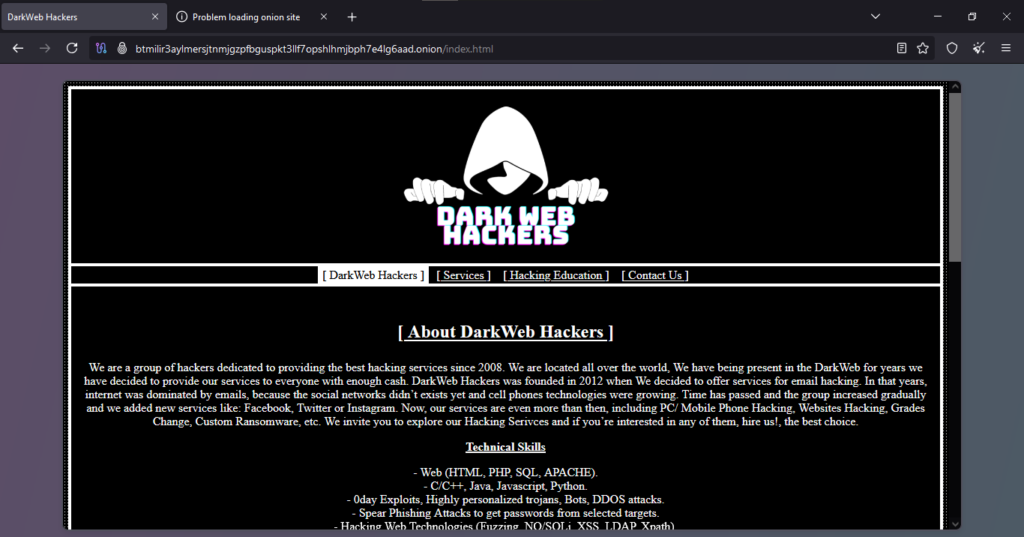
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The client report describes a suspected scam involving a fraudulent hacking service advertised online. According to the report, the user initiated an order to hack an iPhone and made the required payment using Bitcoin. However, after completing the payment, the service provider failed to deliver the promised service. The client highlights that despite repeated follow-ups to obtain updates or support, no information was provided, leaving the order unfulfilled.
This situation illustrates a typical scam scenario on websites advertising illegal or dubious services. The report reflects the user’s frustration and highlights a lack of transparency and accountability on the part of the service provider. The concise nature of the report, while clear in its message, leaves out some critical details, such as the name of the website, the amount paid, or the timeline of the events.
Segment Two: Defining Key Terminology and Terms
To better understand the details of the report, it is important to define the key terms used:
- Hack an iPhone: This refers to gaining unauthorized access to the system or data of an iPhone device. Such actions are illegal and constitute a breach of privacy and cybersecurity laws. Services offering to hack devices are inherently untrustworthy and often fronts for scams.
- Bitcoin (BTC): Bitcoin is a digital cryptocurrency used for transactions on online platforms, including many anonymous or illegal marketplaces. Its pseudonymous nature makes it popular for activities where users seek to avoid traditional financial oversight. However, Bitcoin transactions are irreversible, meaning funds cannot be recovered if sent to scammers.
- Repeated Requests: This phrase indicates the user made multiple attempts to contact the service provider for updates or resolution. A lack of response in such cases often signifies fraudulent intent or operational incompetence.
- Order Not Carried Out: This refers to the failure to deliver the promised service or product after payment has been received. In this context, it highlights a breach of trust and indicates the transaction was likely fraudulent.
Segment Three: Analysis and Recommendations
This report highlights a scenario where the user fell victim to a scam by engaging with an untrustworthy online service provider. The use of Bitcoin as the payment method exacerbated the problem, as its irreversible nature made it impossible to recover the funds once the transaction was completed. Furthermore, the inherently illegal nature of the service offered (hacking an iPhone) means the user is unlikely to seek legal recourse, as doing so would implicate them in attempting to procure unlawful services.
To mitigate similar risks in the future, several actions are recommended:
- Avoid Illicit Services: Users should refrain from engaging with websites or services that advertise illegal activities, as these platforms are often designed to exploit users and carry significant legal and ethical risks.
- Verify Credibility: For any online transaction, especially those involving cryptocurrency, users should conduct thorough research into the provider’s credibility. This includes reviewing feedback from other users, verifying contact information, and assessing the website’s transparency regarding its operations.
- Fraud Prevention Awareness: Public education about the risks of engaging with anonymous online service providers and the potential for scams in the cryptocurrency ecosystem is critical. Users should be aware of red flags, such as a lack of customer support, overly vague terms of service, or unrealistic promises.
- Cybersecurity Practices: Encourage users to prioritize cybersecurity and report scams to relevant authorities or platforms monitoring fraudulent websites. Awareness campaigns and partnerships between cybersecurity organizations and law enforcement can help reduce the prevalence of such scams.
This report underscores the dangers of engaging with anonymous online services and demonstrates how the combination of illegal activity and untraceable payment methods creates a high-risk environment for users. To protect themselves, users should prioritize legal, transparent, and reputable services while avoiding platforms that promise illicit or questionable offerings.