Table of Contents
ToggleDark Web Hackers (7) – TOR Scam Report (125)
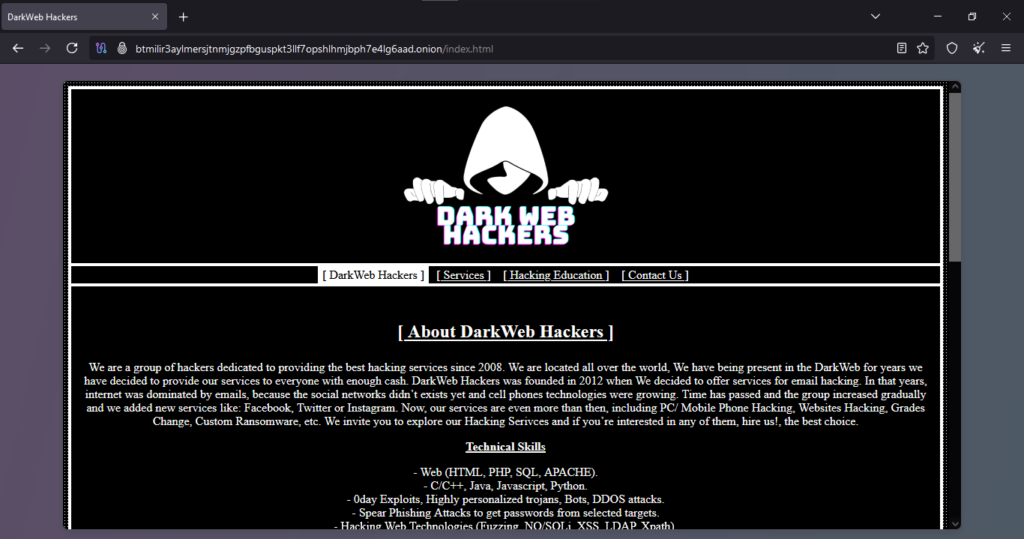
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The client’s report illustrates a common pattern in online scams, where individuals seeking illicit services are lured in by fraudulent promises, only to be abandoned after payment.
The report highlights three key elements: the promise of a service to “hack an iPhone,” payment made via Bitcoin, and the absence of follow-up or delivery after payment. The website in question likely exploited the victim’s interest in obtaining unauthorized services, offering false assurances of expertise and anonymity. The use of Bitcoin as the payment method adds another layer to the scam, as the decentralized and irreversible nature of Bitcoin transactions leaves victims with no ability to reclaim their funds or hold the scammers accountable. This lack of response after repeated inquiries is a classic hallmark of fraudulent schemes operating in the unregulated and anonymous corners of the internet.
Defining Key Terminology
- Hack an iPhone: The term refers to unauthorized access to an Apple iPhone, often involving bypassing security features, accessing sensitive data, or installing malicious software. Such activities are illegal and violate privacy laws, making any service offering these actions both unethical and fraudulent.
- Bitcoin (BTC): A decentralized digital currency that enables peer-to-peer transactions without the need for intermediaries. While its transparency is ensured through blockchain technology, Bitcoin transactions are irreversible, and users remain pseudonymous. These features make Bitcoin attractive for scams and illegal transactions, as they minimize the chances of tracing or recovering stolen funds.
- Repeated Requests for Follow-up: This indicates the victim’s attempts to contact the scammer or website after payment, which were ignored. Fraudulent platforms often cease communication immediately after receiving payment, exploiting the buyer’s inability to escalate or enforce accountability.
By examining these terms, it becomes clear how the scam was executed. The website used the illegal appeal of iPhone hacking to lure the victim and Bitcoin’s untraceable nature to secure payment. Once the payment was made, the scammers likely “ghosted” the victim, leaving them with no further updates or recourse.
Lessons and Recommendations
This scam report serves as a cautionary example of the risks associated with engaging in illicit online transactions. The promise of hacking services may appear enticing to those seeking unauthorized access, but these offers are not only illegal but also rife with opportunities for scammers to exploit unsuspecting individuals. The victim in this case suffered a financial loss due to the inherent risks of dealing with unverified websites and using cryptocurrency for payment.
To prevent falling victim to similar schemes, the following precautions should be considered:
- Avoid Illegal Transactions: Attempting to purchase unauthorized services, such as hacking, is unethical and illegal. Engaging in such activities can lead to legal consequences and financial losses.
- Understand Cryptocurrency Risks: Bitcoin and other cryptocurrencies lack consumer protections. Payments are irreversible, and there is no central authority to mediate disputes or recover funds.
- Verify the Credibility of Online Services: Fraudulent websites often lack transparency, verifiable reviews, or customer support. Before making any transaction, conduct thorough research and assess the platform’s legitimacy.
The client’s experience highlights the vulnerabilities associated with unregulated digital spaces and unethical transactions. Ultimately, educating oneself about the risks of online scams and adhering to ethical practices are crucial to avoiding such losses. This report reinforces the importance of skepticism and diligence when navigating the internet, particularly when money or sensitive information is involved.