Table of Contents
ToggleVeteran-Level Breakdown of Exploit.IN — A Field Report from the Underground
Website
Introduction
Exploit. IT has been in the cyber underground for years, enough to make it among the longest-lived black-hat intelligence and exploit-sharing sites. Except for the fact that this plot is not a pure carding marketplace, it is rather a deep-web knowledge base reporting on exploits, vulnerabilities, hacks, malware, fraud discussions and zero-day leaks!
It is the sum of a newsroom, an intelligence archive, plus a social network of hackers, from SIM-swapping lawsuits to Node. JS vulnerabilities and malware strain analyses, among other things, are where the digital underground, wannabe pentesters, and occasionally even white-hat security researchers peek in from the shadows to stay up to date.
Platform Overview: Key Platform Features
-
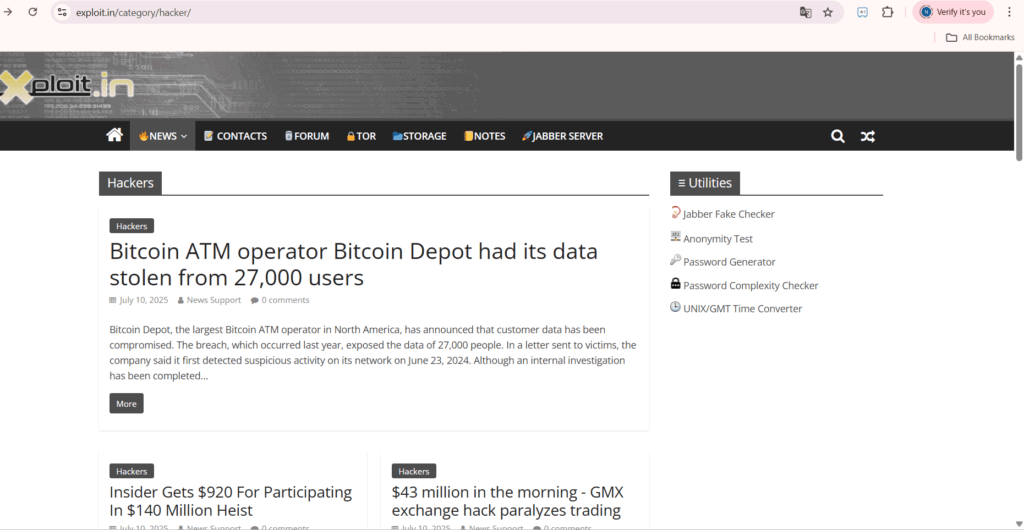
Tabs & Sections: Exploit. IN has organised its dashboard well, with labelled sections such as News, Contacts, Forum, TOR, Storage, Notes, Jabber Server, and topic-based ones like Malware, Carding, Vulnerabilities, and Laws. There are tabs for monitoring live threat intelligence, hacker actions, and rescues. The arrangement is simple and purpose-driven, as opposed to decorative, intended for those with underground experience.
-
Support Structure: Although there is no formal ticketing system, you can rely on forums as an informal support channel. High-rep users usually help the community. The Jabber server handles private communications, but there’s no product issue resolution like conventional shops, as it’s not a CVV source.
-
Primary Content & Intelligence: From deep-dive malware investigations to leaking scoops, the business value is in information, not product sales. Anticipate insider breach narratives, crypto thefts, exploit dumps and developer tool compromises such as the Fake VS Code extension hijacking.
-
Search, Navigation & Language: Although there’s no search engine, it’s easy enough to browse through the forums, which are all well-organised. The language is predominantly Russian and English. Threads navigate quite easily if you are familiar with your standard underground lingo and OPSEC practices.
-
Access & Pricing: Invitation or manual approval is required for registration. It’s an info-sharing platform; therefore, no payment is needed. But in the contacts section, there are Jabber IDs of top sellers of malware, carding, and fraud services.
-
Security Protocols & User Privacy: Anti-OSINT Policy: VPN, TOR, and OPSEC are required. Users are recommended not to enter the site through search engines and should use Jabber with OTR instead.
Dashboard & Sectional Breakdown
-
News: This is a roundup of news and events related to global cybercrime. The stories range from directed malware campaigns to insider heists to leaked credentials from large institutions. Updates are frequent and often reflect new intelligence before it is disseminated into mainstream media.
-
Contacts: Various contact options are available via secured Jabber IDs, moderator handles, and one-way encrypted contacts. Many merchants publish their PGP authenticated public keys.
-
Forum: The Bulletin Board (Forum) is the heart and soul of Exploit. IN where deep discussions are held about zero-days, carding methods, malware builds, and OPSEC. Some veterans and newcomers trade tips, post guides and even argue over police tactics. That’s where the actual learning and networking take place.
-
TOR: Provides official onion mirror links. Monthly verified to prevent phishing releases.
-
Storage: Shared tools, archives, dumps, and longwrites. It contains the PDF leaks, ZIP toolkits, and ISO setups used by malware builders.
-
Notes: Encrypted notes for that user, stored on the account. Use as a place to log credit cards, supplier codes or outstanding actions.
-
Jabber Server: Exploit. IN operates its own Jabber server for users to create an anonymous handle and protect their business.
On-the-Ground Performance: User Perspectives
Veterans swear by it. Not a product-selling shop, Exploit. IN is a place to develop new tools and TTPs (Tactics, Techniques, Procedures). The reputation system is utilised, and there are numerous benefits to a close-knit community, including the regular posting of major cyber news.
There are complaints about slow administrative response, but the community tends to self-manage with the help of moderators and trusted posters.
Pros (Advantages)
- Long-standing, trusted underground presence
- Regular news & threat reports
- In-depth look at malware analysis and real hacker case studies
- Secure Jabber comms
- Free access to exploit information
- Multilingual support: English & Russian
- TOR-safe mirror structure
Cons (Disadvantages)
- No support or resolution desk
- Invite-only access can limit reach
- No product previews, automated vendors
- Primarily text-based; complicated for beginners
- Lacks integration with escrow/payment systems
- Language barrier for non-technical users
Final Words
Exploit. IN is like no ordinary darknet market — it’s more like a hacker’s bastion merged with a showroom for data exploits. Its audience includes the people who study, deploy or defend against subterranean threats. If you’re looking for a card dump store, this ain’t it. But if you want to see what hackers are up to — or draw lessons from breaches before they become headlines — this is a gold mine.
Similar Alternatives
-
RaidForums (Defunct): Formerly the go-to for breaches, now seized by law enforcement.
-
BreachForums (Rebooted version): A new and revitalised RaidForums for everyone. Offers a similar exploit-sharing vibe.
-
CrackingForum: More focused on cracking tools, combos and proxies — but in the same spirit.
Bottom Line
Verdict: LEGIT (For Info Sharing & Threat Intel)
Exploit. IN is a community-based, non-commercial board to keep hacking alive. It does not directly sell CVVs or dumps. Still, the vast array of research-grade material available should make it essential reading for underground analysts, threat hunters, or OPSEC-minded buyers seeking access to vetted vendors via Jabber. Not for beginners — but heaven for the already-in-the-know.