Table of Contents
ToggleDark Web Hackers – TOR Scam Report (87)
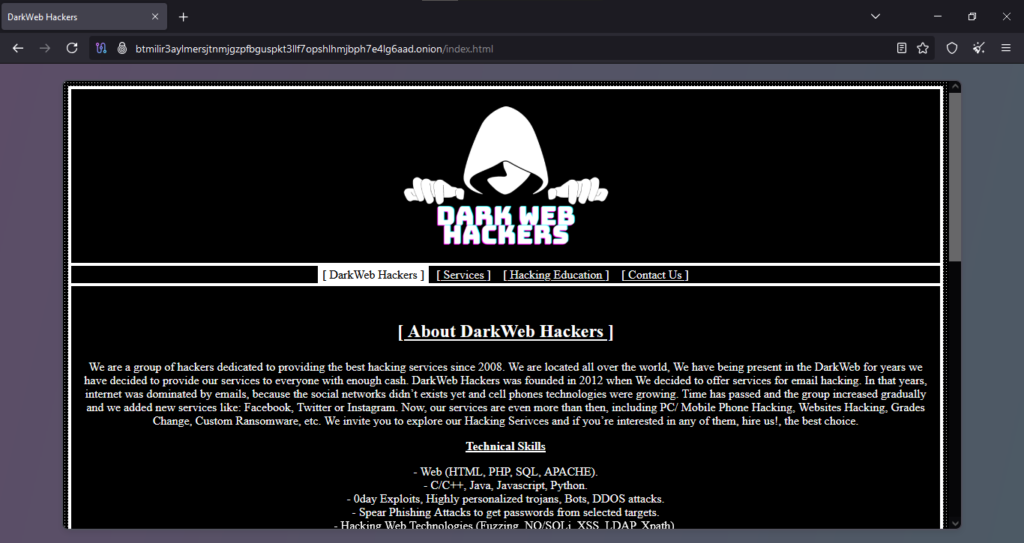
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The original scam report provides a detailed account of a transaction gone wrong on a website that claims to offer hacking services. It is a common issue in fraudulent online services: users pay for promised services, but those services are not delivered, and communication ceases after payment is made.
This report highlights three key issues: (1) the user initiated an order for an illicit service—hacking an iPhone—but it was never completed; (2) payment was made using Bitcoin, a popular yet irreversible method for online transactions; and (3) despite repeated attempts to seek clarification or updates, no responses were provided, leaving the user in a state of financial loss and uncertainty. These elements together indicate a likely scam, where the website is designed to take advantage of individuals seeking unlawful services.
II. Analysis and Definition of Key Terminology
To fully understand the implications of the scam, it is necessary to define the terminology and terms included in the original report:
- Order to Hack an iPhone: This refers to the user’s request for a service to gain unauthorized access to another individual’s iPhone. Such activities are illegal in most jurisdictions, as they constitute a breach of privacy, unauthorized access to personal devices, and potential data theft.
- Paid in Bitcoins: Bitcoin is a cryptocurrency known for its decentralized and pseudonymous nature. While it offers advantages like fast transactions and minimal fees, it is also favored by scammers due to its irreversible transactions and difficulty in tracing. In this context, the user’s payment in Bitcoin means they have little recourse for recovering their funds once the payment is made.
- Repeated Requests: This term refers to the user’s attempts to follow up on the status of their order. The lack of response from the website operators is a common characteristic of scam operations, where communication often ends once payment is received.
- No Further Information: Indicates a complete cessation of communication or updates regarding the service. This tactic is employed by scammers to discourage victims from pursuing further action and to avoid leaving digital traces that could lead to their identification.
III. Implications and Concluding Remarks
The reported incident underscores a recurring pattern in online scams involving illicit services. Websites offering services like phone hacking often serve as traps for individuals willing to pay for unlawful actions. By accepting payment upfront—especially in Bitcoin, which is virtually impossible to recover—the operators of these websites secure their profits without any intention of delivering the promised services. The cessation of communication after payment further signals a deliberate strategy to exploit victims and avoid detection.
This scam report also highlights the risks associated with using cryptocurrency for transactions, particularly when dealing with unverified or illegal platforms. While Bitcoin is legitimate and widely used for lawful purposes, its irreversibility and lack of centralized authority make it a preferred method of payment for scams. Victims who pay in Bitcoin often find themselves without legal or financial recourse.A
In conclusion, this scam serves as a cautionary tale about the dangers of engaging with untrustworthy online platforms, especially those promoting illicit services. It also emphasizes the need for greater awareness of the risks associated with cryptocurrency transactions in potentially fraudulent scenarios. The lack of transparency, refusal to deliver promised services, and the disappearance of communication collectively highlight a calculated effort to defraud. Users are advised to exercise extreme caution when dealing with unknown or dubious platforms and to avoid engaging in illegal activities, as doing so not only makes them targets for scams but also exposes them to legal consequences.