Table of Contents
ToggleDark Web Hackers – TOR Scam Report (117)
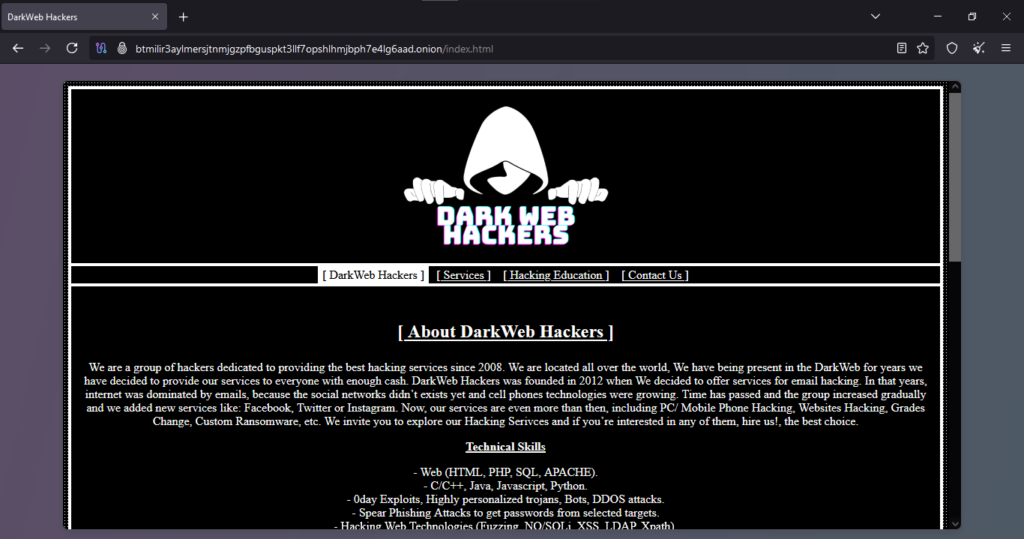
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The original scam report highlights several key aspects of the client’s grievance. The client initiated a transaction on a website, aiming to procure a service to hack an iPhone. They made the payment using Bitcoin, a cryptocurrency known for its pseudonymity, which is often exploited in fraudulent activities. Despite making repeated requests for updates or completion of the service, the client received no response or follow-up, leaving the order unfulfilled. This lack of communication and service delivery forms the crux of their complaint, showcasing dissatisfaction with the website’s handling of their transaction.
Segment 2: Defining Key Terminology
- Order to Hack an iPhone: This phrase refers to the request made by the client for a specific service—hacking an iPhone. It is important to note that such activities are illegal in most jurisdictions and often conducted in the unregulated space of the deep web, where scams are prevalent.
- Paid in Bitcoins: Bitcoin is a decentralized cryptocurrency that allows transactions to be conducted without intermediaries. Its pseudonymity is a double-edged sword: while it offers privacy to users, it is also frequently used in illicit activities, including scams, as it is difficult to trace.
- Repeated Requests: This term highlights the client’s efforts to seek updates or resolution regarding their order. In legitimate transactions, repeated requests typically result in responses or action from the service provider; their absence here underscores a lack of professionalism or fraudulent intent.
- Not Carried Out: This phrase indicates the service was not rendered as promised. It suggests either incompetence or deliberate deception on the part of the website.
- No Further Information: This points to a complete lack of communication from the service provider post-payment, leaving the client without clarity or recourse.
Segment 3: Analysis and Contextual Insights
This report exemplifies a recurring pattern in scams related to illegal or high-risk services advertised online. The client’s intent to purchase a hacking service—a dubious and unlawful activity—made them vulnerable to exploitation. Fraudsters frequently target individuals seeking illegal services, knowing that such victims are less likely to report the scam to authorities due to the nature of the transaction. By leveraging Bitcoin as the payment method, the scammers further ensured the transaction would be irreversible and untraceable, leaving the client with no financial recourse.
The absence of updates or communication after payment is a hallmark of fraudulent operations. Legitimate businesses or service providers, regardless of the legality of their offerings, typically maintain communication with their clients. The lack of response here indicates a deliberate intent to deceive. This case highlights the importance of understanding the risks associated with engaging in illegal activities online, as such transactions often attract scammers who exploit both the anonymity of the internet and the hesitancy of victims to seek legal help.
From a broader perspective, this incident underscores the importance of consumer awareness in online transactions, even in gray or black market spaces. Verifying the legitimacy of vendors, avoiding untraceable payment methods, and recognizing red flags, such as poor communication, can mitigate the risk of falling victim to scams. This report also serves as a cautionary tale: engaging in illegal activities not only poses ethical and legal risks but also increases the likelihood of being defrauded, with little to no recourse available to the victim.