Table of Contents
ToggleDark Web Hackers (6) – TOR Scam Report (124)
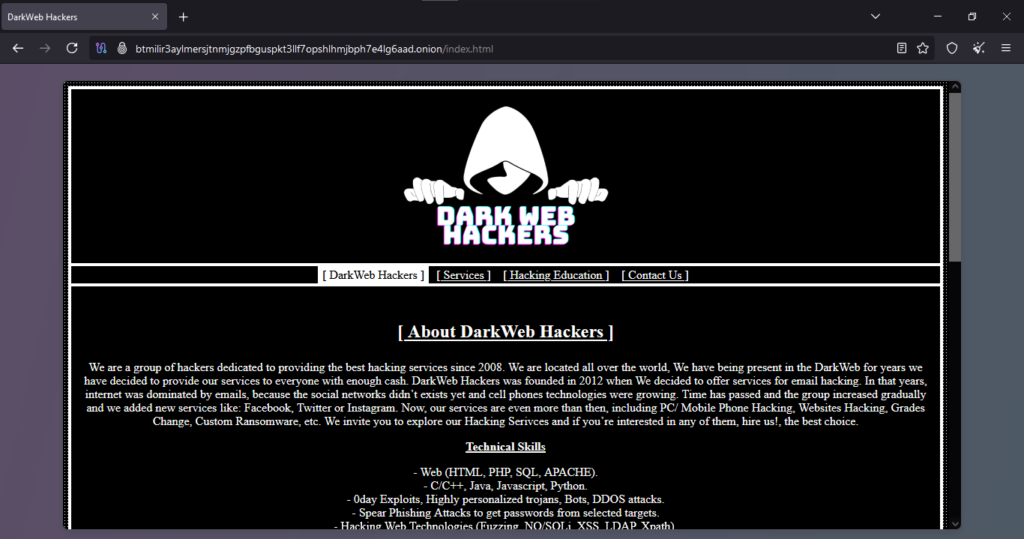
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Thank you for reading this post, don't forget to subscribe!Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The report describes an individual attempting to acquire an illicit hacking service through an unverified website. Upon making the required Bitcoin payment, the service was either not delivered or contact ceased, which is a common outcome in fraudulent transactions involving illegal services.
The key elements of this scam report include the enticing offer of hacking services and the use of Bitcoin as the payment method. The promise to hack an iPhone likely appealed to the client due to its perceived complexity and exclusivity, creating the illusion of credibility. However, the lack of regulation and accountability in such transactions often leaves buyers with no means of recovering their funds once payment has been made. The report implicitly highlights how scammers exploit the anonymity of cryptocurrency and the demand for illegal services to victimize users.
Defining Key Terminology
- Hacking an iPhone: Refers to unauthorized access or control over an Apple iPhone, often involving techniques such as exploiting vulnerabilities, bypassing security measures, or installing spyware. These services are illegal and unethical, as they violate privacy laws and cybersecurity regulations.
- Bitcoin (BTC): A decentralized digital currency that operates without a central authority. Bitcoin transactions are recorded on a public ledger (blockchain) but remain pseudonymous, making it difficult to trace the identity of the parties involved. This feature makes Bitcoin a popular payment method in scams and illicit transactions.
- Unverified Websites: Websites that operate without any credible oversight or verification. They often claim to offer exclusive services or products, such as hacking, counterfeit goods, or stolen accounts. These platforms lack consumer protection mechanisms, leaving users vulnerable to fraud.
The use of Bitcoin in this report is significant because it demonstrates how scammers leverage its irreversibility and anonymity to facilitate fraudulent activities. The concept of hacking an iPhone is another red flag, as such services are not only illegal but also lack legitimacy in the technical community. These terms highlight the risks inherent in engaging with unethical and unregulated platforms.
Lessons and Recommendations
This report underscores the dangers of attempting to procure illegal services online. Scammers often lure potential victims with promises of exclusive or difficult-to-obtain services, exploiting both the buyer’s curiosity and the lack of oversight in cryptocurrency-based transactions. The client’s experience illustrates how these transactions are structured to benefit the scammer, with no accountability or possibility of recourse for the buyer.
To avoid falling victim to similar schemes, individuals should adhere to the following best practices:
- Refrain from Engaging in Illegal Activities: Attempting to purchase hacking services is not only unethical but also exposes the buyer to significant legal and financial risks.
- Be Cautious with Cryptocurrency Payments: Understand that Bitcoin transactions are irreversible and offer no consumer protection. Always verify the legitimacy of the platform and service before making any payment.
- Avoid Unverified Platforms: Scammers frequently use unregulated websites to advertise fraudulent services. Conduct thorough research, including reviews and testimonials, to assess the credibility of any platform.
The client’s experience is a critical reminder that engaging with unverified platforms and illicit services poses substantial risks. While the allure of such services might be strong, the consequences far outweigh any perceived benefits. Education, skepticism, and adherence to ethical principles are essential tools for avoiding similar scams in the future.