Table of Contents
ToggleDark Web Hackers – TOR Scam Report (25)
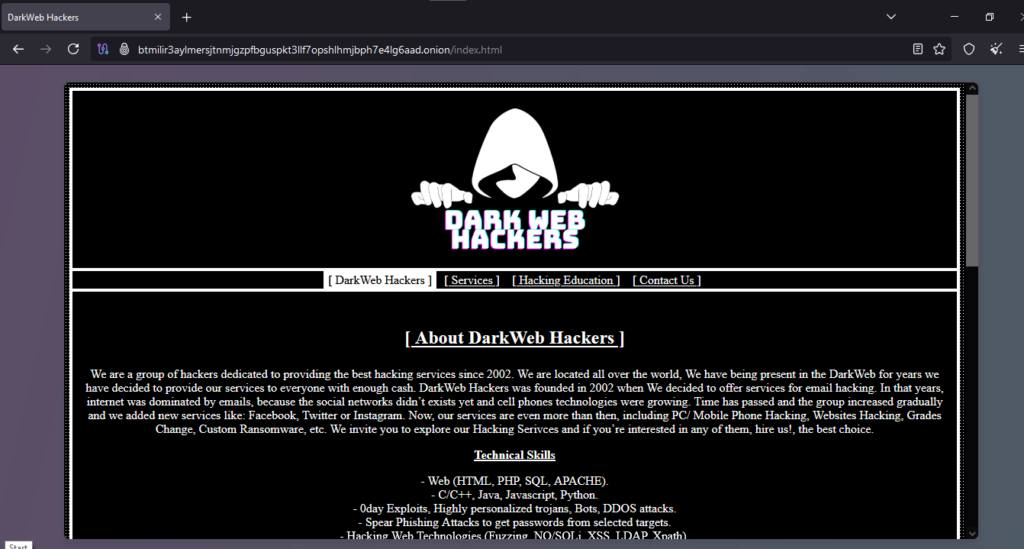
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
This report describes a transaction involving a payment in Bitcoin for a hacking service that was not fulfilled. The user indicates they attempted to follow up with the website but received no response or updates about the status of their order. This lack of communication, combined with the unfulfilled service, suggests the user was a victim of an online scam.
Defined Terminology and Key Issues
Breaking down key terms and concepts from the report provides greater clarity about the nature of the alleged scam:
- Order to Hack an iPhone: The user engaged in an illegal activity by seeking to hack an iPhone. Hacking services are often advertised on dubious websites, particularly on the dark web or other unregulated online platforms. These services are not only unethical but are also illegal in most jurisdictions.
- Paid in Bitcoins: Bitcoin is a decentralized digital currency often used in online transactions due to its anonymity and ease of use. Scammers frequently prefer Bitcoin payments because transactions are irreversible, making it nearly impossible for victims to recover their funds once transferred.
- Repeated Requests: This phrase indicates that the user attempted to follow up with the website’s operators multiple times. Scammers often ignore these follow-ups, relying on the lack of accountability in anonymous online environments to avoid responding.
- Order Not Carried Out: This confirms that the service promised—hacking an iPhone—was never delivered. Non-fulfillment of a paid order is a classic characteristic of online scams.
- No Further Information: The user’s complaint that they received no updates suggests either neglect or a deliberate tactic by scammers to sever communication after payment is received.
These terms and phrases highlight key aspects of scams involving illegal services: a promise of unethical outcomes, the use of irreversible payment methods, and a lack of communication or resolution when the scam is exposed.
Report Context and Implications
The user’s report highlights several red flags common to scams on platforms offering illegal services. Websites that advertise services such as hacking are inherently untrustworthy because they operate outside legal boundaries and ethical norms. Victims of these scams are particularly vulnerable, as they are unlikely to report their experience to authorities due to their involvement in illegal activities.
The use of Bitcoin as a payment method is a hallmark of scams, especially on unregulated platforms. Scammers exploit the irreversible nature of cryptocurrency transactions, knowing that once funds are received, victims have no legal recourse to recover their money. This incident underscores the risks associated with engaging in illegal online transactions, both in terms of financial loss and potential legal repercussions.
In conclusion, this report serves as a cautionary example of the risks associated with attempting to procure illegal services online. It highlights the ease with which scammers exploit the anonymity of cryptocurrency and the lack of accountability in illegal marketplaces. While the user’s intention to hack an iPhone was itself unethical and unlawful, their experience emphasizes the broader dangers of interacting with unverified platforms. This case reinforces the importance of staying within legal and ethical boundaries when navigating online transactions to avoid financial loss, legal consequences, and potential victimization by scams.