Table of Contents
ToggleDark Web Hackers – TOR Scam Report (29)
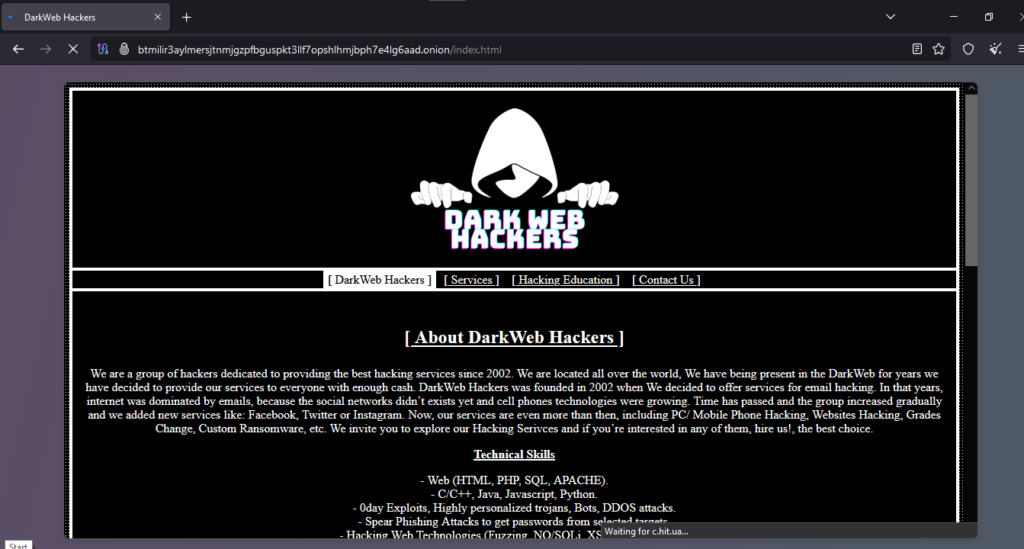
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The scam report details an unsuccessful attempt to procure an iPhone hacking service via an online website. According to the client, the service was paid for using Bitcoin, a popular cryptocurrency for anonymous transactions. Despite completing the payment and making multiple follow-up requests, the client received no further communication or progress updates regarding the order. This lack of response after payment suggests a classic fraudulent operation, in which scammers advertise a service, collect payment, and then vanish without delivering the promised product or service. The report highlights the common elements of such scams: a lack of transparency, unfulfilled promises, and complete abandonment of communication after funds are secured.
Defining Key Terminology
Understanding this scam requires unpacking several critical terms used in the report. “Hacking an iPhone” refers to unauthorized access to an Apple iPhone’s data or functions. This can involve bypassing security measures to extract private information, install spyware, or gain control of the device’s features. While such services are illegal and unethical, they are often advertised in underground markets as tools for surveillance or personal revenge. The payment was made using Bitcoin, a decentralized digital currency widely used in online transactions, particularly on dark web marketplaces. Bitcoin transactions are irreversible and typically anonymous, making it a favored choice for scammers who want to avoid detection and deny refunds. The absence of further communication post-payment is a hallmark of scams in this space, where accountability is minimal and users operate under pseudonyms.
Detailed Analysis and Implications
This incident showcases the inherent risks of engaging with services advertised in online underground or gray markets. The promise of a highly sensitive and illegal service like hacking creates a dynamic in which the client is unlikely to report the fraud to authorities due to potential legal repercussions. Scammers exploit this dynamic, knowing that victims have limited avenues for recourse. Additionally, the use of Bitcoin ensures that the transaction is irreversible, leaving the victim with no ability to recover their funds. This double layer of anonymity and irreversibility emboldens scammers to continue such fraudulent operations with minimal fear of consequences.
For potential clients considering similar services, this case serves as a cautionary tale. The combination of illegal services, anonymous payment methods, and unregulated marketplaces creates an environment ripe for scams. A lack of verifiable credentials, transparent communication, or guarantees should serve as immediate red flags. This breakdown not only highlights the need for greater awareness of scam tactics but also underscores the broader implications of engaging in illicit transactions. Individuals seeking such services may not only lose their funds but also expose themselves to additional risks, including blackmail or legal issues.