Table of Contents
ToggleDark Web Hackers – TOR Scam Report (52)
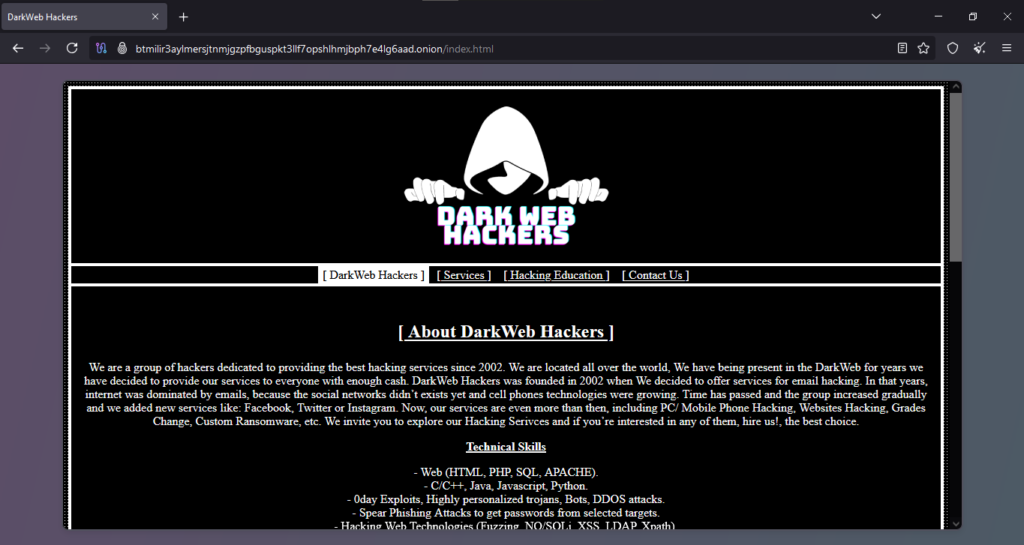
Onion Link : http://btmilir3aylmersjtnmjgzpfbguspkt3llf7opshlhmjbph7e4lg6aad.onion/index.html
Scam Report Date : 2024-11-18
Client Scam Report Breakdown
Original Scam Report :
The client report outlines a scam scenario in which a user attempted to procure an iPhone hacking service via a website. According to the report, the user initiated the order and made payment using Bitcoin, but the service was never delivered. Additionally, the user made repeated attempts to obtain updates or a resolution, but the website failed to provide any further information. This absence of communication, coupled with the undelivered service, solidifies the operation as fraudulent.
This report illustrates a common pattern within online scams, particularly those involving illicit services. The platform’s use of cryptocurrency, a payment method frequently favored for its anonymity and irreversibility, serves as a critical component of the scam. By failing to deliver the promised service and ignoring follow-up inquiries, the scammer capitalizes on the challenges victims face in seeking recourse.
Segment 2: Defining Key Terminology
Understanding the mechanics of this scam requires defining the key terms and processes described in the report:
- Order to Hack an iPhone: The promised service involves compromising an Apple device’s security, an illegal activity that is often marketed on unregulated platforms. These “services” are commonly used as bait to attract unsuspecting customers.
- Paid in Bitcoins: Bitcoin is a decentralized cryptocurrency that provides pseudonymity and is irreversible once confirmed. Scammers exploit these features to make it nearly impossible for victims to trace or recover funds.
- Repeated Requests: Refers to the victim’s follow-up attempts to obtain information or a resolution. Scammers often ignore such inquiries to avoid confrontation or provide vague responses to prolong the victim’s hope.
- No Further Information: A deliberate tactic by the scammer to cease communication, leaving the victim without clarity or options for recourse.
The combination of these elements highlights a deliberate strategy that exploits both the victim’s desperation and the inherent challenges of engaging with anonymous, unregulated platforms.
Segment 3: Analysis and Implications
This case exemplifies how scammers exploit the anonymity of digital currencies and the lack of oversight on platforms offering illicit services. The scam hinges on several psychological and logistical factors, including the victim’s perceived inability to report the crime due to its illegal nature and the irreversible nature of Bitcoin payments. By refusing to provide further updates or explanations, the scammer ensures that the victim is left isolated and without actionable options.
From a preventive standpoint, education is a crucial tool to mitigate such scams. Potential buyers of such services must be aware that platforms advertising illegal services are often scams themselves. Additionally, the anonymity of cryptocurrency payments is a double-edged sword; while it offers privacy, it also eliminates avenues for financial recovery in fraud cases. Victims of such scams are encouraged to document their experience and report it to cybersecurity agencies, which can use the data to identify and dismantle fraudulent networks.
For law enforcement and cybersecurity experts, this report underscores the importance of monitoring platforms advertising illegal activities. Addressing such scams involves collaboration between cryptocurrency exchanges, law enforcement agencies, and cybersecurity organizations to track and analyze fraudulent payment flows. Efforts to educate users about the risks of engaging with these platforms are equally critical in reducing the prevalence of such scams. The key takeaway is that trust should never be extended to anonymous platforms advertising illegal services, as the risk of victimization far outweighs any potential reward.